Introduction
In the world of creating websites, making sure that only the right people can access certain parts of a site is really important. That’s where JSON Web Tokens (JWT) come in handy. They’re like special passes that web applications give to users to prove they’re allowed to see or do certain things without needing to constantly check back with the server. In ASP.NET Core 6, using JWT for this kind of authentication and authorization is a big deal. It means your site can handle lots of users without slowing down, and it keeps everything safe too.
In this guide, we’re going to dig deep into how to use JWT for authentication and authorization in ASP.NET Core 6. We’ll start with the basics of what JWT is and how it works, then move on to practical stuff like how to set it up and use it effectively. Plus, we’ll talk about some smart ways to integrate JWT into your ASP.NET Core 6 projects to make them even better. It’s going to be a comprehensive journey through all things JWT and ASP.NET Core 6!
Exploring JSON Web Tokens (JWT)
JSON Web Tokens (JWT) are like compact, secure passes shared between two parties. They’re designed to be safe for use in URLs and consist of three main parts: a header, a payload, and a signature. The header usually tells you what kind of token it is and how it’s been signed. The payload is where you find all the important info about the user, like their ID, what they’re allowed to do, and when the token expires. Finally, the signature is like a seal of approval, ensuring the token hasn’t been messed with or altered in any way. Understanding how JWTs work is key to using them effectively in web development.
Key Concepts of JWT:
- Claims: Claims are statements about an entity (typically, the user) and additional data. Claims are represented as key-value pairs in the payload of the JWT.
- Signing: JWTs can be signed using a secret key or a public/private key pair. Signing ensures the integrity and authenticity of the token. Signed JWTs can be verified using the same key used for signing.
- Expiration: JWTs can have an expiration time (exp claim) after which they are considered invalid. This helps mitigate security risks associated with long-lived tokens.
Implementing JWT Authentication in ASP.NET Core 6
Now, let’s explore how to implement JWT authentication and authorization in ASP.NET Core 6:
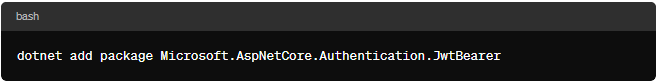
Step 1: Install Required Packages
To implement JWT authentication in ASP.NET Core 6, you’ll need to install the Microsoft.AspNetCore.Authentication.JwtBearer package:
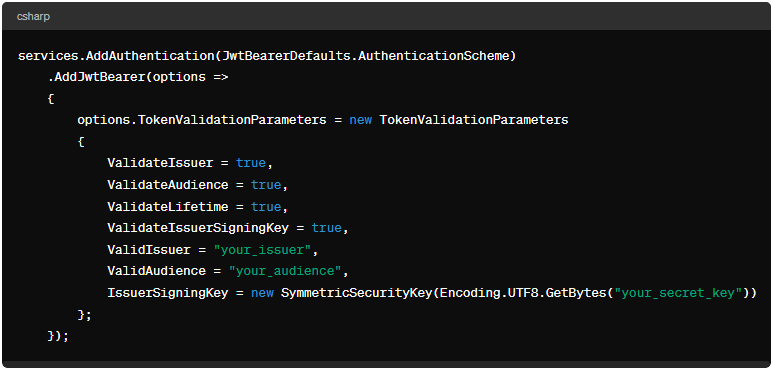
Step 2: Configure JWT Authentication
In the Startup.cs file, configure JWT authentication services and options:
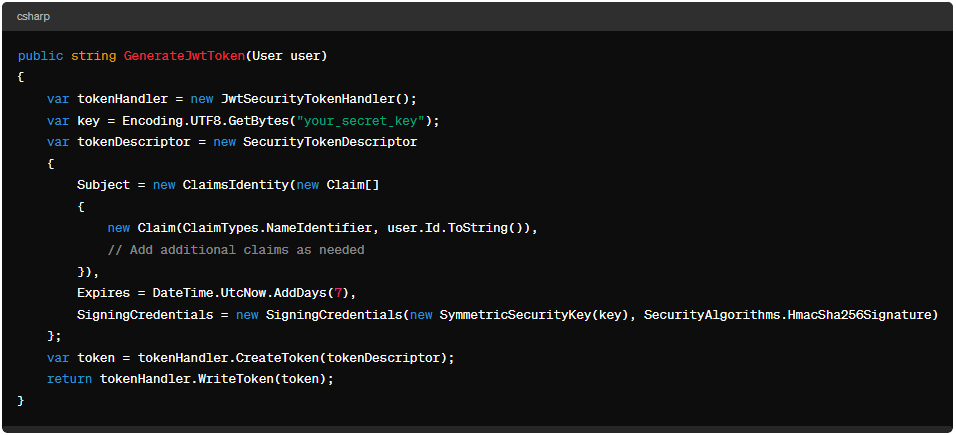
Step 3: Generate JWT Tokens
Implement a method to generate JWT tokens upon successful user authentication. Use the JwtSecurityTokenHandler class to create and sign JWT tokens:
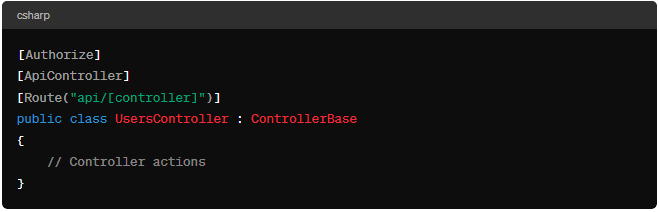
Step 4: Secure Endpoints with JWT Authentication
Secure your API endpoints or controller actions by applying the [Authorize] attribute:
Best Practices for JWT Authentication
To ensure the security and reliability of JWT authentication in ASP.NET Core 6, follow these best practices:
- Use HTTPS: Always use HTTPS to encrypt communication between clients and servers when using JWT tokens to prevent token leakage or tampering.
- Validate Tokens: Validate JWT tokens on every request to ensure that they are not expired, have a valid signature, and are issued by a trusted authority.
- Use Strong Secret Keys: Use strong secret keys for signing JWT tokens to prevent unauthorized access or token forgery.
- Implement Token Revocation: Implement token revocation mechanisms, such as token blacklisting or token expiration, to mitigate the risk of token misuse or theft.
- Keep Payloads Small: Minimize the size of JWT payloads by including only essential claims to reduce the risk of token tampering or interception.
Conclusion
In ASP.NET Core 6, mastering authentication and authorization using JSON Web Tokens (JWT) provides a powerful and scalable solution for securing web applications. By understanding the fundamentals of JWT, implementing JWT authentication, and following best practices, developers can ensure the security and reliability of their ASP.NET Core 6 applications. Whether you’re building APIs, microservices, or full-fledged web applications, JWT authentication offers flexibility, extensibility, and robust security features. With ASP.NET Core 6 and JWT, you can confidently build and deploy secure web applications that meet the needs of today’s demanding users. Happy coding and stay secure!
